⚔️ Protect your API
Logto is an off-the-shelf authorization service that enables you to enforce authorization on your backend API resources , enhancing their privacy protection.
Register the API resources
To obtain an audience-restricted access_token from Logto, you must register your backend APIs. When an authorization request is received, Logto will identify the registered API resources and grant access accordingly.
To register your APIs, navigate to the API Resources section in the console. You will see a built-in resource with the API identifier displayed as https://[your-tenant-id].logto.app/api. This resource encompasses all the Management APIs of Logto and ensures that they are protected and accessible only to authorized users of Logto.
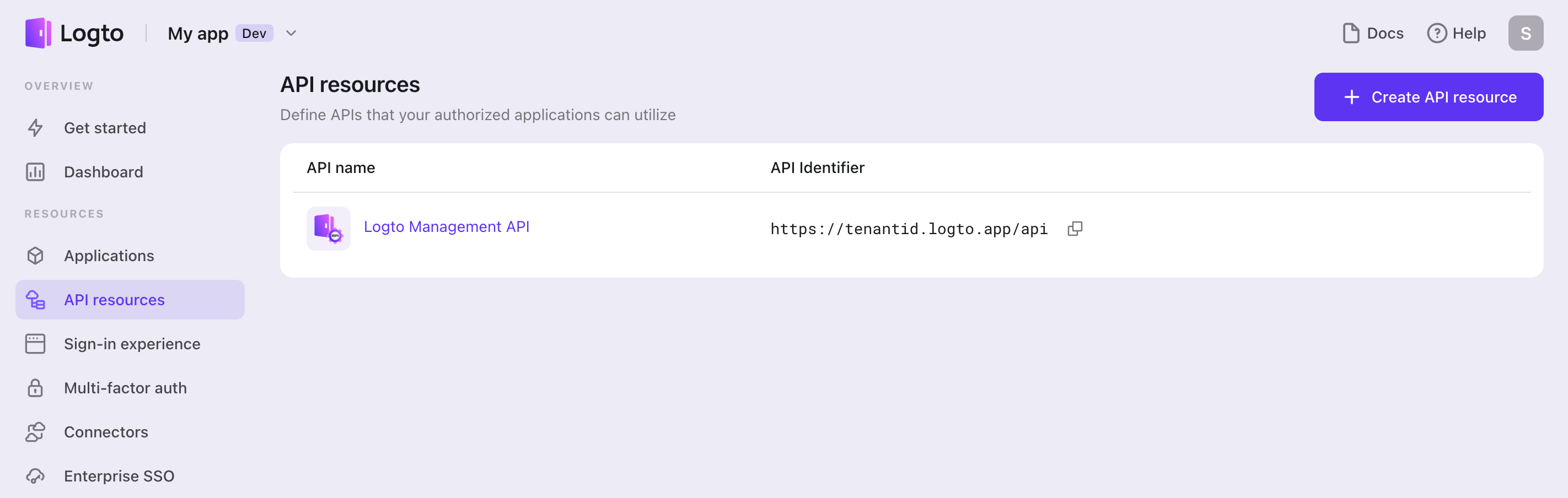
Click on the Create API Resource button and following the interactive form to create your own API resources:
- A human-readable API Name that may better helps you to identify this entity.
- A unique API Identifier (a.k.a. Resource Indicator) in URI format. It represents the identity of the API resource.
The API Identifier is unique and used as the single source of truth for Logto, and it's NOT editable once created. Be careful when you create it.
The new API will show up on the list once created. You may manage or delete it at the API details page by clicking on the entity.
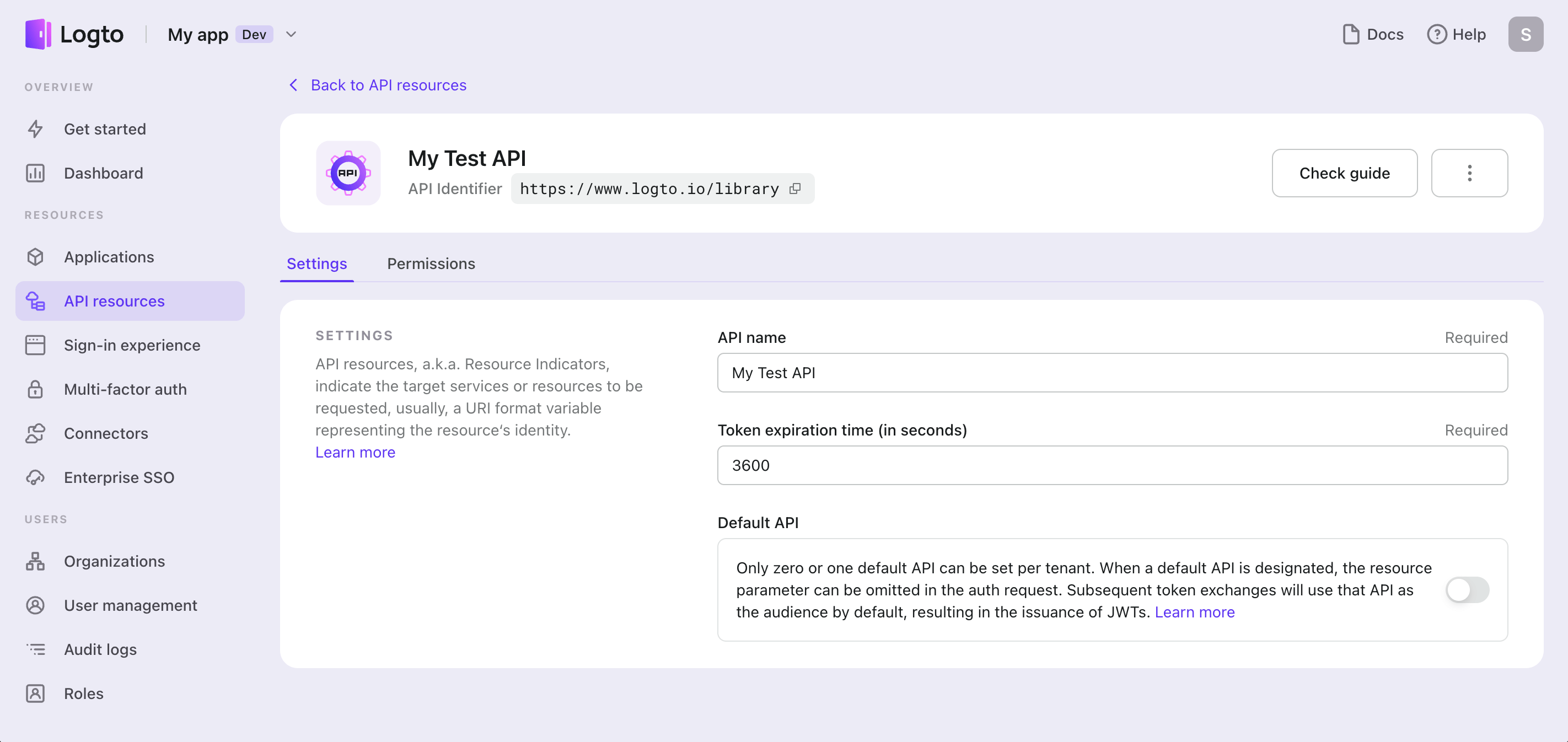
See API Resource Logto Schema for detailed API setting definitions.
The API Resources registered in Logto Admin Console will be shared across all your applications.
Permissions and RBAC
See 🔐 RBAC for details.
Validate the API request's authorization token
Logto issues a standard JWT format authorization token for each authorized API request. The token is encrypted and signed as a JWS token.
Understanding JWS token
An encoded JWS token is constructed with three parts:
- JOSE Header: Declares the code type and encoding algorithm
- JWS Payload: Includes all the token's claims
- JWS Signature: Signature signed with JWK
A standard schema of Logto issued JWS Payload: (claims may vary, based on your custom OIDC config)
| key | description |
|---|---|
| jti | unique JWT ID |
| sub | subject, usually user-id |
| iat | timestamp token issues at |
| exp | timestamp token expires at |
| client_id | application id |
| iss | token issuer identity |
| aud | audience of the token |
| scope | scopes (permissions) of the token |
For development, to visually inspect a JWT token, you could visit jwt.io to decode and check the tokens you received. Be careful with or never use the tokens from a production environment. As this is a third party provided public online service, your token may be exposed.
Validate the authorization token
- Validating a JWT
- Validating the JWS signature
- The token's issuer is
https://<your-logto-domain>/oidc(issued by your Logto auth server) - The token's audience is equal to the current receiver's resource indicator registered in Logto Admin Console
- The token is within its expiration time
- (🔐 RBAC only) The token has the desired
scope
There are various open-source libraries and packages that can help you to validate and decode a JWT token easily. You may pick one and integrate with your backend application based on the language and framework you are using. Please check some of the examples we have:
Reference
Logto uses the code-based OAuth 2.0 Authorization Protocol to make your API request safe. If you are interested in the strategy behind it, refer to OAuth 2.0's specification for more details.